ACCESS CONTROL
NODER Access Control has been developed on the basis of many years of experience in the field of physical security systems. It offers unprecedented flexibility in design, installation and use for this type of system. It is free from the typical problems and disadvantages of other access control systems. The NODER access control system has end-to-end encryption, i.e. encryption of communication from the card (and also mobile credentials) to the server, management and visualisation of the system.
This makes it possible to build a comprehensive solution that meets each level (1-4 grades) of the IEC 60839-11-1 standard.
Flexibility of NODER access control system is characterised by:
- Supports up to 12 readers by a single controller
- Each controller is an independent IP device based on Linux OS
- Unlimited number of controllers in the system
- Easy installation, no need to install intermediate
- Local preview of current controller operating parameters
- Versatility in connection of RS-485 readers
- Unlimited possibilities to create user rights
- Off-line mode with the same possibilities as on-line mode
- Possibility to control intruder alarm systems from NODER readers
- Shared user management with other security systems
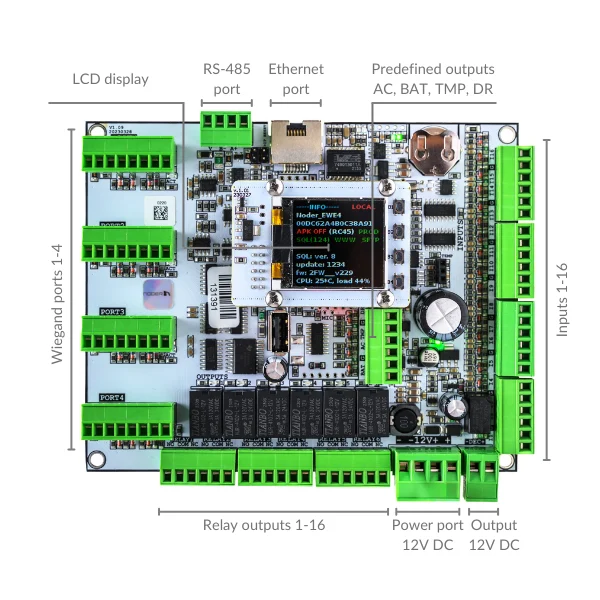
RS-485 port for connection of NODER’S RS-485 readers, OSDP readers or additional control modules.
1 of 9Ethernet port for connecting the controller to the structured network.
2 of 9 Special outputs:AC – no AC
BAT – battery operation
TMP – failure of the 12V DC power supply
DR – enclosure door opening
3 of 9
12V DC power supply
4 of 912V power output for connection and control of readers power supply
5 of 9Relay outputs 1-16
6 of 9Inputs 1-16
7 of 9Wiegand ports 1-4
8 of 9LCD display
9 of 9CONTROLLERS
There are EWE4-LCD, EWE4 and EE12 controllers, which are fully autonomous devices based on the Linux operating system. In addition, they are equipped with a microprocessor for the management and operation of inputs, relay outputs and reader communication buses. The controllers store off-line:
- schedules
- access levels
- scripts
- events
- other information necessary for the controller to operate offline
In the event of a loss of communication with the server, the controllers will still allow authorised users access to the protected areas, together with a record of events in the built-in local memory, which can store more than 2 million logs. The decision to allow access to a protected area (e.g. after an employee’s card has been read by the readers) can be made directly by the controller itself (unless set otherwise), which ensures an immediate reaction to the fact that the card has been inserted into the reader and, for example, the door lock has been released.
The controller’s operations are independent of the availability and quality of communication with the server. When the connection to the server is re-established, all events stored in the controller are automatically downloaded from the server and stored in the system database. This allows events to be stored for any length of time, limited only by the capacity of the hard drives installed in the server. Changing controller, reader and user settings is instantaneous and does not interrupt system operation!
European Access Control
EWE4, EWE4-LCD and EE12 controllers are designed and made in Europe!
Communication protocols with proximity readers
NODER controllers have the ability to connect readers using several communication protocols. The possibilities are shown in the table below:
| Controller model | RS-485 readers (NODER) | RS-485 readers (OSDP) | Wiegand readers |
| EWE4 | Yes | Yes | Yes |
| EWE4-LCD | Yes | Yes | Yes |
| EE12 | Yes | Yes | No |
NODER access control can
IMMEDIATE CHANGE OF SETTINGS AND USERS
PROXIMITY READERS
Readers are based on the secure MIFARE DESFire RFID card standard and NFC with the possibility of granting access via a mobile app NODER Mobile Access. However, the connection between the readers and the controller is via the RS-485 protocol for MD-R and MDK-R readers, and communication is encrypted using the AES-256 algorithm.
Proximity readers support
MIFARE DESFire and NFC technology
Individual encryption keys are generated for each access control system for reader-to-card and reader-to-mobile application transmission to ensure maximum security of the access control system by making it impossible to swap the access control reader or RFID card end device.
For customized applications, e.g. as a key depository or printer access reader, the MD-W reader is available, communicating via the Wiegand protocol. This reader, like all NODER readers, supports the MIFARE DESFire card standard.
Modern access control systems must adapt to the non-standard requirements of our customers, that is why we offer the NODER QR-W reader. These allow bar code or QR code reading, which is most often used as temporary access to e.g. a conference room. Through integration with third-party systems such as the queue system and the use of bar code readers, it is possible to grant temporary access depending on the queue to which a person has been assigned.
SYSTEM FUNCTIONALITIES
European Access Control
Our proximity readers are designed and made in Europe!
User management
- supervision over connections with controllers and the state of connected peripheries
- configuration of controllers and access control transitions
- monitoring of statuses and events in the system with the accuracy of a single door
- accepted or rejected access
- entrance or exit
- waiting for passage
- no passage after using authorized card
- operating mode (normal, unlocked reader)
- strain
- too long holding the door
- switching to battery operation
- sabotage of the controller’s casing
- control from the map level (view of the building):
- one-time passage opening
- permanent unlocking the passage
- permission to access (in the case of working in dual access mode – with the operator’s confirmation)
- possibility of individual control of controller outputs
- displaying the image from the camera observing the passage after clicking the chosen camera icon on the map
- automatic display of a camera or several cameras assigned to a chosen passage after clicking the door icon on the map
Managements software
- creating rules of permissions and schedules
- adding users and granting permissions
- automatic filling the field with the card number in cooperation with a dedicated USB reader or from any reader in the system
- data update, blocking or deleting users
- creating and granting rights for user groups (departments)
- assigning photo to a user (from a file or by capturing a picture from any camera in the system)
- quick cards printing using previously prepared templates
- quick search for users, schedules, access levels
- ability to create any user types which will contain various, individually created data fields (Employees, Guests, Customers, etc.)
- ability to restrict operator’s access to selected data user (invisible, read, read and record)
- granting operators the ability to create, delete and modify users / departments
- creating users with the Anti-pass-back function
- locating users
- ability to import or export users to other systems (txt, csv, Excel, database file)
- cooperation with the “Event Manager” module enabling eg. photo identification or access in dual mode. Examples of action scenarios:
- Tracking events, related only to specific access control passage. The security guard tracks events only from the passages he is responsible for, at the same time only events that are relate to selected passages are displayed on the screen
- Photoidentifiation. When the security guard walks nerby the passage, on the screen displayes a picture of a passing employee, connected with his identifier. The security guard approves access via the software interface or by pressing the door open buton connected directly to the controller
- Photo- and videoidentyfication. When the security guard is far from the access point. While identifying employees (card reading), not only their photographs, but also videos from the appropriate camera appear on the screen of the security guard. No matter how far away the work station is from the passage, the security guard can grant access after comparing photographs and videos
- Displaying special information about employees. While identifying an employee, any information stored in his file can be displayed on the security guard’s screen. For example next to basic information such as photo, name, position etc. on the screen might be an information if the employee can bring a laptop with him
- A central point of tracking of disturbing events, which is displaying the status of access points on the map and automatically displaying the video from the corresponding camera. In a central supervisory position, only disturbing events ar usually dispalyed, such as burglary or changing the status of connection with controllers etc. As their number is small, therefore the station may serve at the same time more passages. All events are real-time displayed on the map with the video from a specific camera
Guard Route System
By using the NODER Access Control Management System, we have the ability to track the presence of security guards at specific points within a building or area.
LOW CURRENT DESIGNER!
We have prepared battery capacity selection form
Calculate the current requirements of the individual system components and select the appropriate batteries for the designed NODER access control system.
MIFARE DESFire
Radio Frequency IDentification (RFID) technologies are playing an increasingly important role in our daily lives in the face of growing data security challenges. The MIFARE standard, developed by NXP Semiconductors, addresses these challenges by offering advanced security and flexibility solutions.
Several versions of MIFARE technology are available on the market, including MIFARE Classic, Plus, Ultralight and DESFire. Each of these standards has its own unique set of features and security levels. MIFARE DESFire stands out as the most secure and flexible, capable of supporting multiple applications on a single card. Standards such as MIFARE Classic, while once popular, have proven vulnerable to various attacks and cloning such a card is currently not a problem. This has led to the development of more advanced standards, such as MIFARE DESFire, which offer much better protection against data security threats. MIFARE DESFire is a technology that uses advanced encryption algorithms to provide a very high level of data security. This encryption protects the information transmitted between the card and the reader, preventing unauthorised access and data manipulation.
MIFARE standards comparison
- MIFARE Classic: The most widely used standard, revolutionary at the time of its introduction, but now considered insecure.
- MIFARE Plus: An improved version of MIFARE Classic that offers greater security. Now considered insecure.
- MIFARE Ultralight: A lightweight version for ticketing and identification systems where cost is more important than security complexity. Currently considered insecure
- MIFARE DESFire: The most advanced standard, the choice for applications requiring high security and multi-functionality.
Why choose DESFire?
Door Access Control System based on the MIFARE DESFire standard is the preferred choice for those who require the highest level of data protection. Its advanced security, flexibility and ability to integrate with different systems make it the ideal solution for modern, intelligent access control systems. The choice of this standard is justified not only by its advanced security features, but also by its versatility and flexibility, which are essential in rapidly evolving access control systems. Its features make MIFARE DESFire the ideal solution for organisations looking for reliable and secure RFID technology.
MIFARE DESFire offers a number of advanced features that are key to the security and performance of RFID systems. These include:
- Applications: The ability to support multiple applications on a single card, increasing flexibility and convenience.
- Encryption: Provides data protection from generation to verification, which is essential to prevent attacks and card cloning.
- Personalisation: The ability to customise cards to meet an organisation’s specific needs, enabling better integration with existing systems.
- Scalability: Easy expansion and adaptation of RFID systems to meet growing security and functionality requirements.
Access control and NFC mobile credentials in the NODER Mobile Access app

NFC (Near Field Communication) is a short-range technology that allows two electronic devices to communicate wirelessly over a distance of a few centimetres. NFC enables NODER access control users to use their smartphones as access credentials, replacing or supplementing traditional physical cards. Such a solution increases user convenience and eliminates the need to handle physical cards.
The future of access control
RFID technology is constantly evolving and the MIFARE DESFire standard plays a key role in this process. Its advanced security features and flexibility make it the standard of choice for modern access control systems by organisations around the world. The DESFire standard is the future of RFID technology, offering unparalleled security and flexibility. Its advanced features and capabilities make it the ideal choice for any organisation looking to protect its data and access control systems against today’s threats.



